Dhole Moments
open_in_new https://soatok.blog/feed/
Software, Security, Cryptography, and Furries
Feed Info
[2026-02-02T22:36:27.441Z] Updated feed with 20 items
[https://soatok.blog/feed/]
Copy Link
Grid View
List View
Flow View

Software Assurance & That Warm and Fuzzy Feeling
If I were to recommend you use a piece of cryptography-relevant software that I created, how would you actually know if it was any good? Trust is, first and foremost, a social problem. If I told you a furry designed a core piece of Internet infrastructure, the reception to this would be mixed, to say […]

Practical Collision Attack Against Long Key IDs in PGP
In response to the GPG.Fail attacks, a Hacker News user made this claim about the 64-bit “Long Key IDs” used by OpenPGP and GnuPG, while responding to an answer I gave to someone else’s question: OK, to be clear, I am specifically contending that a key fingerprint does not include collisions. My proof is empirical, that no […]

Everything You Need to Know About Email Encryption in 2026
If you think about emails as if they’re anything but the digital equivalent of a postcard–that is to say, postcards provide zero confidentiality–then someone lied to you and I’m sorry you had to find out from a furry blog that sometimes talks about applied cryptography. At the end of 2025, at the 39th Chaos Communications […]

The Revolution Will Not Make the Hacker News Front Page
(with apologies to Gil Scott-Heron) If you get all of your important technology news from “content aggregators” like Hacker News, Lobste.rs, and most subreddits, you might be totally unaware of the important but boring infrastructure work happening largely on the Fediverse, indie web, and other less-centralized communities. This is no accident. The rough consensus of […]

Announcing Key Transparency for the Fediverse
I’m pleased to announce the immediate availability of a reference implementation for the Public Key Directory server. This software implements the Key Transparency specification I’ve been working on since last year, and is an important stepping stone towards secure end-to-end encryption for the Fediverse. You can find the software publicly available on GitHub: To get […]

Moving Beyond the NPM elliptic Package
Why replace the elliptic package? Yesterday, the Trail of Bits blog published a post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using Wycheproof. This blog post was accompanied by a new chapter in their Testing Handbook about using Wycheproof as well as two CVEs. It’s pretty cool work, […]

The Dreamseeker’s Vision of Tomorrow
Since I have your attention for the moment, I’d like you to ask yourself a question: What is it that drives you in life? Do you yearn for the feeling of safety? By seeking power, status, wealth, and fame? Is it cravings for pleasure that motivate your actions? Does a sense of obligation to others, […]

Are You Under the Influence? The Tail That Wags The Dog
It is tempting and forgivable to believe that we’re in control of our social media experiences. After all, we write what we want in our bio, select our avatars, and even come up with our own handles. We decide who we follow, what we post, and which recommendations to consider. It never feels like we’re […]

It’s a Cold Day in Developer Hell, So I Must Roll My Own Crypto
I have several projects in-flight, and I wanted to write a quick status update for them so that folks can find it easier to follow along. Please bear in mind: This is in addition to, and totally separate from, my full-time employment. Hell Frozen Over A while ago, annoyed by the single point of failure […]

Barking Up The Ratchet Tree – MLS Is Neither Royal Nor Nude
One of the first rules you learn about technical writing is, “Know your audience.” But often, this sort of advice is given without sufficient weight or practical examples. Instead, you’re ushered quickly onto the actual tactile aspects of writing–with the hope that some seed was planted that will sprout later in your education. Science communication […]
Improving Geographical Resilience For Distributed Open Source Teams with FREEON
In a recent blog post, I laid out the argument that, if you have securely implemented end-to-end encryption in your software, then the jurisdiction where your ciphertext is stored is almost irrelevant. Where jurisdiction does come into play, unfortunately, is where your software is developed and whether or not the local government will employ rubber-hose […]

Age Verification Doesn’t Need to Be a Privacy Footgun
“Won’t someone think of the poor children?” they say, clutching their pearls as they enact another stupid law that will harm the privacy of every adult on Earth and create Prior Restraint that inhibits the freedom of speech in liberal democracies. If you’re totally ignorant of how things work, the proposal of “verifying you’re an […]

Against the Censorship of Adult Content By Payment Processors
This is a furry blog, where I write about whatever interests me and sign it with my fursona’s name. I sometimes talk about furry fandom topics, but I sometimes also talk about applied cryptography. If you got a mild bit of emotional whiplash from that sentence, the best list of posts to start reading to […]

Jurisdiction Is Nearly Irrelevant to the Security of Encrypted Messaging Apps
Every time I lightly touch on this point, I always get someone who insists on arguing with me about it, so I thought it would be worth making a dedicated, singular-focused blog post about this topic without worrying too much about tertiary matters. Here’s the TL;DR: If you actually built your cryptography properly, you shouldn’t […]
Checklists Are The Thief Of Joy
I have never seen security and privacy comparison tables (henceforth referred to simply as “checklists” for brevity) used for any other purpose but deception. After pondering this observation, I’m left seriously doubting if these checklists have any valid use case except to manipulate the unsuspecting. Please keep in mind that I’m talking about something very […]
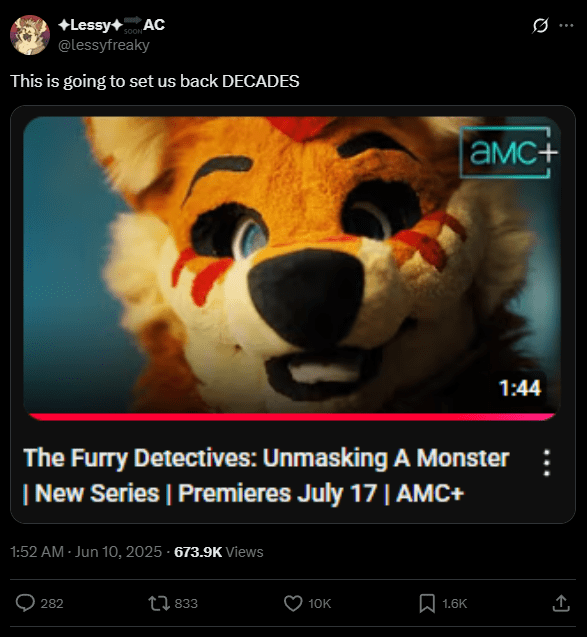
Furries Need To Learn That Sunlight Is The Best Disinfectant
Next month, AMC+ is premiering a new series about furries that tracked down sexual abusers hiding within the furry fandom. It’s called, The Furry Detectives: Unmasking A Monster. You can watch the trailer for this below. And I do recommend watching the trailer before reading the rest of this blog post. Done? Okay. Bad Takes […]

What Does It Even Mean To Be “Great” Anyway?
I normally don’t like writing “Current Events” pieces (and greatly prefer focusing on what SEO grifters like to call “evergreen content”), but I feel this warrants it. Content warning: Violence, death, mentions of political extremism. What Does “Great” Mean? Imagining living under constant threats of having your house burned down for 2 years, because your […]

Tech Companies Apparently Do Not Understand Why We Dislike AI
It’s becoming increasingly apparent that one of the reasons why tech companies are so enthusiastic about shoving AI into every product and service is that they fundamentally do not understand why people dislike AI. I will elaborate. I was recently made aware of the Jetbrains developer ecosystem survey, which included a lot of questions about […]

Retrospective: Five Years Blogging About Cryptography as a Gay Furry Online
The history of this blog might very well be a cautionary tail (sic) about scope creep. The Original Vision For Dhole Moments Originally, I just wanted a place to write about things too long for Twitter (back when I was an avid Twitter poster). I also figured, if nothing else, it would be a good […]

The Authenticity Drought
The types of people that proudly call themselves “influencers,” and describe what they create merely as “content,” are so profoundly allergic to authenticity that it bewilders the mind. Don’t believe me? Look no further than the usage of “unalive” in the modern lexicon. The verb “unalive” became a thing because content creators (predominantly on YouTube) […]

The Practical Limitations of End-to-End Encryption
Internet discussions about end-to-end encryption are plagued by misunderstandings, misinformation, and some people totally missing the point. Of course, people being wrong on the Internet isn’t exactly news. Yesterday, a story in The Atlantic alleged that the Trump Administration accidentally added their editor, Jeffrey Goldberg, to a Signal group chat discussing a military action in […]

Post-Quantum Cryptography Is About The Keys You Don’t Play
(With severe apologies to Miles Davis.) Post-Quantum Cryptography is coming. But in their haste to make headway on algorithm adoption, standards organizations (NIST, IETF) are making a dumb mistake that will almost certainly bite implementations in the future. Sophie Schmieg wrote about this topic at length and Filippo Valsorda suggested we should all agree to […]

On The Insecurity of Telecom Stacks in the Wake of Salt Typhoon
Towards the end of last year, we learned that a group (allegedly affiliated with the Chinese government, referred to as “Salt Typhoon”) breached T-Mobile and other telecommunications companies and caused all sorts of havoc. This isn’t really a blog post about that incident, but it was the catalyst that inspired a bit of curiosity within […]

Shaming Isn’t Shielding: The Moral Panics That Cry Wolf
Content Warning: This blog post talks about adult themes and sexuality. If you’re under 18, sit this one out. If you’ve been around the furry fandom for a while, you will notice that discourse tends to have a cyclical nature to it. I’ve written about this topic before. More than once. And even covered it […]

Reviewing the Cryptography Used by Signal
Last year, I urged furries to stop using Telegram because it doesn’t actually provide them with any of the privacy guarantees they think it gives them. Instead of improving Telegram’s cryptography to be actually secure, the CEO started spreading misleading bullshit about Signal®. Since then, I’ve been flooded with people asking me about various other […]

Hell Is Overconfident Developers Writing Encryption Code
Overconfident developers that choose to write their own cryptography code have plagued the information security industry since before it was even an industry. This in and of itself isn’t inherently a bad thing, despite the infosec truisms about never doing exactly that. Writing crypto code (but not deploying or publishing it!) is an important first […]

Too Many People Don’t Value the Time of Security Researchers
It’s really not my place to ever command respect from anyone; and that’s not just because I’m a furry–which has always been towards the bottom of the geek hierarchy. I am well aware how little weight my words truly carry, even to other furries, as well as how little I really matter. But the tech […]

Software Assurance & That Warm and Fuzzy Feeling
If I were to recommend you use a piece of cryptography-relevant software that I created, how would you actually know if it was any good? Trust is, first and foremost, a social problem. If I told you a furry designed a core piece of Internet infrastructure, the reception to this would be mixed, to say […]

Practical Collision Attack Against Long Key IDs in PGP
In response to the GPG.Fail attacks, a Hacker News user made this claim about the 64-bit “Long Key IDs” used by OpenPGP and GnuPG, while responding to an answer I gave to someone else’s question: OK, to be clear, I am specifically contending that a key fingerprint does not include collisions. My proof is empirical, that no […]

Everything You Need to Know About Email Encryption in 2026
If you think about emails as if they’re anything but the digital equivalent of a postcard–that is to say, postcards provide zero confidentiality–then someone lied to you and I’m sorry you had to find out from a furry blog that sometimes talks about applied cryptography. At the end of 2025, at the 39th Chaos Communications […]

The Revolution Will Not Make the Hacker News Front Page
(with apologies to Gil Scott-Heron) If you get all of your important technology news from “content aggregators” like Hacker News, Lobste.rs, and most subreddits, you might be totally unaware of the important but boring infrastructure work happening largely on the Fediverse, indie web, and other less-centralized communities. This is no accident. The rough consensus of […]

Announcing Key Transparency for the Fediverse
I’m pleased to announce the immediate availability of a reference implementation for the Public Key Directory server. This software implements the Key Transparency specification I’ve been working on since last year, and is an important stepping stone towards secure end-to-end encryption for the Fediverse. You can find the software publicly available on GitHub: To get […]

Moving Beyond the NPM elliptic Package
Why replace the elliptic package? Yesterday, the Trail of Bits blog published a post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using Wycheproof. This blog post was accompanied by a new chapter in their Testing Handbook about using Wycheproof as well as two CVEs. It’s pretty cool work, […]

The Dreamseeker’s Vision of Tomorrow
Since I have your attention for the moment, I’d like you to ask yourself a question: What is it that drives you in life? Do you yearn for the feeling of safety? By seeking power, status, wealth, and fame? Is it cravings for pleasure that motivate your actions? Does a sense of obligation to others, […]

Are You Under the Influence? The Tail That Wags The Dog
It is tempting and forgivable to believe that we’re in control of our social media experiences. After all, we write what we want in our bio, select our avatars, and even come up with our own handles. We decide who we follow, what we post, and which recommendations to consider. It never feels like we’re […]

It’s a Cold Day in Developer Hell, So I Must Roll My Own Crypto
I have several projects in-flight, and I wanted to write a quick status update for them so that folks can find it easier to follow along. Please bear in mind: This is in addition to, and totally separate from, my full-time employment. Hell Frozen Over A while ago, annoyed by the single point of failure […]

Barking Up The Ratchet Tree – MLS Is Neither Royal Nor Nude
One of the first rules you learn about technical writing is, “Know your audience.” But often, this sort of advice is given without sufficient weight or practical examples. Instead, you’re ushered quickly onto the actual tactile aspects of writing–with the hope that some seed was planted that will sprout later in your education. Science communication […]

Improving Geographical Resilience For Distributed Open Source Teams with FREEON
In a recent blog post, I laid out the argument that, if you have securely implemented end-to-end encryption in your software, then the jurisdiction where your ciphertext is stored is almost irrelevant. Where jurisdiction does come into play, unfortunately, is where your software is developed and whether or not the local government will employ rubber-hose […]

Age Verification Doesn’t Need to Be a Privacy Footgun
“Won’t someone think of the poor children?” they say, clutching their pearls as they enact another stupid law that will harm the privacy of every adult on Earth and create Prior Restraint that inhibits the freedom of speech in liberal democracies. If you’re totally ignorant of how things work, the proposal of “verifying you’re an […]

Against the Censorship of Adult Content By Payment Processors
This is a furry blog, where I write about whatever interests me and sign it with my fursona’s name. I sometimes talk about furry fandom topics, but I sometimes also talk about applied cryptography. If you got a mild bit of emotional whiplash from that sentence, the best list of posts to start reading to […]

Jurisdiction Is Nearly Irrelevant to the Security of Encrypted Messaging Apps
Every time I lightly touch on this point, I always get someone who insists on arguing with me about it, so I thought it would be worth making a dedicated, singular-focused blog post about this topic without worrying too much about tertiary matters. Here’s the TL;DR: If you actually built your cryptography properly, you shouldn’t […]

Checklists Are The Thief Of Joy
I have never seen security and privacy comparison tables (henceforth referred to simply as “checklists” for brevity) used for any other purpose but deception. After pondering this observation, I’m left seriously doubting if these checklists have any valid use case except to manipulate the unsuspecting. Please keep in mind that I’m talking about something very […]

Furries Need To Learn That Sunlight Is The Best Disinfectant
Next month, AMC+ is premiering a new series about furries that tracked down sexual abusers hiding within the furry fandom. It’s called, The Furry Detectives: Unmasking A Monster. You can watch the trailer for this below. And I do recommend watching the trailer before reading the rest of this blog post. Done? Okay. Bad Takes […]

What Does It Even Mean To Be “Great” Anyway?
I normally don’t like writing “Current Events” pieces (and greatly prefer focusing on what SEO grifters like to call “evergreen content”), but I feel this warrants it. Content warning: Violence, death, mentions of political extremism. What Does “Great” Mean? Imagining living under constant threats of having your house burned down for 2 years, because your […]

Tech Companies Apparently Do Not Understand Why We Dislike AI
It’s becoming increasingly apparent that one of the reasons why tech companies are so enthusiastic about shoving AI into every product and service is that they fundamentally do not understand why people dislike AI. I will elaborate. I was recently made aware of the Jetbrains developer ecosystem survey, which included a lot of questions about […]

Retrospective: Five Years Blogging About Cryptography as a Gay Furry Online
The history of this blog might very well be a cautionary tail (sic) about scope creep. The Original Vision For Dhole Moments Originally, I just wanted a place to write about things too long for Twitter (back when I was an avid Twitter poster). I also figured, if nothing else, it would be a good […]

The Authenticity Drought
The types of people that proudly call themselves “influencers,” and describe what they create merely as “content,” are so profoundly allergic to authenticity that it bewilders the mind. Don’t believe me? Look no further than the usage of “unalive” in the modern lexicon. The verb “unalive” became a thing because content creators (predominantly on YouTube) […]

The Practical Limitations of End-to-End Encryption
Internet discussions about end-to-end encryption are plagued by misunderstandings, misinformation, and some people totally missing the point. Of course, people being wrong on the Internet isn’t exactly news. Yesterday, a story in The Atlantic alleged that the Trump Administration accidentally added their editor, Jeffrey Goldberg, to a Signal group chat discussing a military action in […]

Post-Quantum Cryptography Is About The Keys You Don’t Play
(With severe apologies to Miles Davis.) Post-Quantum Cryptography is coming. But in their haste to make headway on algorithm adoption, standards organizations (NIST, IETF) are making a dumb mistake that will almost certainly bite implementations in the future. Sophie Schmieg wrote about this topic at length and Filippo Valsorda suggested we should all agree to […]

On The Insecurity of Telecom Stacks in the Wake of Salt Typhoon
Towards the end of last year, we learned that a group (allegedly affiliated with the Chinese government, referred to as “Salt Typhoon”) breached T-Mobile and other telecommunications companies and caused all sorts of havoc. This isn’t really a blog post about that incident, but it was the catalyst that inspired a bit of curiosity within […]

Shaming Isn’t Shielding: The Moral Panics That Cry Wolf
Content Warning: This blog post talks about adult themes and sexuality. If you’re under 18, sit this one out. If you’ve been around the furry fandom for a while, you will notice that discourse tends to have a cyclical nature to it. I’ve written about this topic before. More than once. And even covered it […]

Reviewing the Cryptography Used by Signal
Last year, I urged furries to stop using Telegram because it doesn’t actually provide them with any of the privacy guarantees they think it gives them. Instead of improving Telegram’s cryptography to be actually secure, the CEO started spreading misleading bullshit about Signal®. Since then, I’ve been flooded with people asking me about various other […]

Hell Is Overconfident Developers Writing Encryption Code
Overconfident developers that choose to write their own cryptography code have plagued the information security industry since before it was even an industry. This in and of itself isn’t inherently a bad thing, despite the infosec truisms about never doing exactly that. Writing crypto code (but not deploying or publishing it!) is an important first […]

Too Many People Don’t Value the Time of Security Researchers
It’s really not my place to ever command respect from anyone; and that’s not just because I’m a furry–which has always been towards the bottom of the geek hierarchy. I am well aware how little weight my words truly carry, even to other furries, as well as how little I really matter. But the tech […]

Software Assurance & That Warm and Fuzzy Feeling
If I were to recommend you use a piece of cryptography-relevant software that I created, how would you actually know if it was any good? Trust is, first and foremost, a social problem. If I told you a furry designed a core piece of Internet infrastructure, the reception to this would be mixed, to say […]

Practical Collision Attack Against Long Key IDs in PGP
In response to the GPG.Fail attacks, a Hacker News user made this claim about the 64-bit “Long Key IDs” used by OpenPGP and GnuPG, while responding to an answer I gave to someone else’s question: OK, to be clear, I am specifically contending that a key fingerprint does not include collisions. My proof is empirical, that no […]

Everything You Need to Know About Email Encryption in 2026
If you think about emails as if they’re anything but the digital equivalent of a postcard–that is to say, postcards provide zero confidentiality–then someone lied to you and I’m sorry you had to find out from a furry blog that sometimes talks about applied cryptography. At the end of 2025, at the 39th Chaos Communications […]

The Revolution Will Not Make the Hacker News Front Page
(with apologies to Gil Scott-Heron) If you get all of your important technology news from “content aggregators” like Hacker News, Lobste.rs, and most subreddits, you might be totally unaware of the important but boring infrastructure work happening largely on the Fediverse, indie web, and other less-centralized communities. This is no accident. The rough consensus of […]

Announcing Key Transparency for the Fediverse
I’m pleased to announce the immediate availability of a reference implementation for the Public Key Directory server. This software implements the Key Transparency specification I’ve been working on since last year, and is an important stepping stone towards secure end-to-end encryption for the Fediverse. You can find the software publicly available on GitHub: To get […]

Moving Beyond the NPM elliptic Package
Why replace the elliptic package? Yesterday, the Trail of Bits blog published a post about finding cryptographic bugs in the elliptic library (a Javascript package on NPM) by using Wycheproof. This blog post was accompanied by a new chapter in their Testing Handbook about using Wycheproof as well as two CVEs. It’s pretty cool work, […]

The Dreamseeker’s Vision of Tomorrow
Since I have your attention for the moment, I’d like you to ask yourself a question: What is it that drives you in life? Do you yearn for the feeling of safety? By seeking power, status, wealth, and fame? Is it cravings for pleasure that motivate your actions? Does a sense of obligation to others, […]

Are You Under the Influence? The Tail That Wags The Dog
It is tempting and forgivable to believe that we’re in control of our social media experiences. After all, we write what we want in our bio, select our avatars, and even come up with our own handles. We decide who we follow, what we post, and which recommendations to consider. It never feels like we’re […]

It’s a Cold Day in Developer Hell, So I Must Roll My Own Crypto
I have several projects in-flight, and I wanted to write a quick status update for them so that folks can find it easier to follow along. Please bear in mind: This is in addition to, and totally separate from, my full-time employment. Hell Frozen Over A while ago, annoyed by the single point of failure […]

Barking Up The Ratchet Tree – MLS Is Neither Royal Nor Nude
One of the first rules you learn about technical writing is, “Know your audience.” But often, this sort of advice is given without sufficient weight or practical examples. Instead, you’re ushered quickly onto the actual tactile aspects of writing–with the hope that some seed was planted that will sprout later in your education. Science communication […]

Improving Geographical Resilience For Distributed Open Source Teams with FREEON
In a recent blog post, I laid out the argument that, if you have securely implemented end-to-end encryption in your software, then the jurisdiction where your ciphertext is stored is almost irrelevant. Where jurisdiction does come into play, unfortunately, is where your software is developed and whether or not the local government will employ rubber-hose […]

Age Verification Doesn’t Need to Be a Privacy Footgun
“Won’t someone think of the poor children?” they say, clutching their pearls as they enact another stupid law that will harm the privacy of every adult on Earth and create Prior Restraint that inhibits the freedom of speech in liberal democracies. If you’re totally ignorant of how things work, the proposal of “verifying you’re an […]

Against the Censorship of Adult Content By Payment Processors
This is a furry blog, where I write about whatever interests me and sign it with my fursona’s name. I sometimes talk about furry fandom topics, but I sometimes also talk about applied cryptography. If you got a mild bit of emotional whiplash from that sentence, the best list of posts to start reading to […]

Jurisdiction Is Nearly Irrelevant to the Security of Encrypted Messaging Apps
Every time I lightly touch on this point, I always get someone who insists on arguing with me about it, so I thought it would be worth making a dedicated, singular-focused blog post about this topic without worrying too much about tertiary matters. Here’s the TL;DR: If you actually built your cryptography properly, you shouldn’t […]

Checklists Are The Thief Of Joy
I have never seen security and privacy comparison tables (henceforth referred to simply as “checklists” for brevity) used for any other purpose but deception. After pondering this observation, I’m left seriously doubting if these checklists have any valid use case except to manipulate the unsuspecting. Please keep in mind that I’m talking about something very […]

Furries Need To Learn That Sunlight Is The Best Disinfectant
Next month, AMC+ is premiering a new series about furries that tracked down sexual abusers hiding within the furry fandom. It’s called, The Furry Detectives: Unmasking A Monster. You can watch the trailer for this below. And I do recommend watching the trailer before reading the rest of this blog post. Done? Okay. Bad Takes […]

What Does It Even Mean To Be “Great” Anyway?
I normally don’t like writing “Current Events” pieces (and greatly prefer focusing on what SEO grifters like to call “evergreen content”), but I feel this warrants it. Content warning: Violence, death, mentions of political extremism. What Does “Great” Mean? Imagining living under constant threats of having your house burned down for 2 years, because your […]

Tech Companies Apparently Do Not Understand Why We Dislike AI
It’s becoming increasingly apparent that one of the reasons why tech companies are so enthusiastic about shoving AI into every product and service is that they fundamentally do not understand why people dislike AI. I will elaborate. I was recently made aware of the Jetbrains developer ecosystem survey, which included a lot of questions about […]

Retrospective: Five Years Blogging About Cryptography as a Gay Furry Online
The history of this blog might very well be a cautionary tail (sic) about scope creep. The Original Vision For Dhole Moments Originally, I just wanted a place to write about things too long for Twitter (back when I was an avid Twitter poster). I also figured, if nothing else, it would be a good […]

The Authenticity Drought
The types of people that proudly call themselves “influencers,” and describe what they create merely as “content,” are so profoundly allergic to authenticity that it bewilders the mind. Don’t believe me? Look no further than the usage of “unalive” in the modern lexicon. The verb “unalive” became a thing because content creators (predominantly on YouTube) […]

The Practical Limitations of End-to-End Encryption
Internet discussions about end-to-end encryption are plagued by misunderstandings, misinformation, and some people totally missing the point. Of course, people being wrong on the Internet isn’t exactly news. Yesterday, a story in The Atlantic alleged that the Trump Administration accidentally added their editor, Jeffrey Goldberg, to a Signal group chat discussing a military action in […]

Post-Quantum Cryptography Is About The Keys You Don’t Play
(With severe apologies to Miles Davis.) Post-Quantum Cryptography is coming. But in their haste to make headway on algorithm adoption, standards organizations (NIST, IETF) are making a dumb mistake that will almost certainly bite implementations in the future. Sophie Schmieg wrote about this topic at length and Filippo Valsorda suggested we should all agree to […]

On The Insecurity of Telecom Stacks in the Wake of Salt Typhoon
Towards the end of last year, we learned that a group (allegedly affiliated with the Chinese government, referred to as “Salt Typhoon”) breached T-Mobile and other telecommunications companies and caused all sorts of havoc. This isn’t really a blog post about that incident, but it was the catalyst that inspired a bit of curiosity within […]

Shaming Isn’t Shielding: The Moral Panics That Cry Wolf
Content Warning: This blog post talks about adult themes and sexuality. If you’re under 18, sit this one out. If you’ve been around the furry fandom for a while, you will notice that discourse tends to have a cyclical nature to it. I’ve written about this topic before. More than once. And even covered it […]

Reviewing the Cryptography Used by Signal
Last year, I urged furries to stop using Telegram because it doesn’t actually provide them with any of the privacy guarantees they think it gives them. Instead of improving Telegram’s cryptography to be actually secure, the CEO started spreading misleading bullshit about Signal®. Since then, I’ve been flooded with people asking me about various other […]

Hell Is Overconfident Developers Writing Encryption Code
Overconfident developers that choose to write their own cryptography code have plagued the information security industry since before it was even an industry. This in and of itself isn’t inherently a bad thing, despite the infosec truisms about never doing exactly that. Writing crypto code (but not deploying or publishing it!) is an important first […]

Too Many People Don’t Value the Time of Security Researchers
It’s really not my place to ever command respect from anyone; and that’s not just because I’m a furry–which has always been towards the bottom of the geek hierarchy. I am well aware how little weight my words truly carry, even to other furries, as well as how little I really matter. But the tech […]